.png?width=128&name=unnamed%20(1).png)
Overview
PolySwarm’s threat research team has discovered new, previously unpublished versions of the EventBot malware family.
EventBot is a family of Android banking trojans that injects credential theft routines into victim bank and web browser applications on infected devices and bypasses SMS 2FA reading incoming SMS.
The newly discovered versions (0.4.0.2 - 0.4.2.6) expand on EventBot’s capabilities, adding:
- contact list theft
- (potential) propagation via SMS
- expanded victim application support, impacting additional victim organizations
- updated command & control (C2) configuration
This post provides some background on EventBot’s evolution and details our findings into the new EventBot versions.
The anti-malware community is invited to hunt for and download samples of these new versions of EventBot for free at https://polyswarm.network.
At present, EventBot targets 364 applications (and growing) with sensitive information using a combination of techniques: SMS theft, keylogging, and bank fraud execution via web injects.
We based our study on 70 EventBot samples from a version history that begins in March 2020. These are currently marked as emerging threats on https://polyswarm.network and are available programmatically via the PolySwarm CLI.
.png?width=630&name=unnamed%20(2).png)
About EventBot
There are already plenty of blogs detailing how EventBot families behave from the reverse engineering perspective and we largely skip these details.
The trojan uses two configurations, one static, embedded in the apk, and one dynamic, the one that has to be downloaded from the C2 URL taken from the static config, and is decrypted according to the following method.
The Encryption/Decryption used for both communication with C2 and the dynamic configuration requests/responses is a novel and more advanced compared to other Android malware. To initialize this encrypted channel the malware uses a session key for getting Dynamic Configuration update along with data exfiltration and standard communication. C2 communication appears as if it is a plaintext http request, but the traffic is encrypted with RC4 and Curve25519 is used to protect the session key for the stream cipher. The Curve25519 key is derived from a static secret in the binary. A key is generated per session in every post/response with the C2.
This one-time session key technique makes it harder to emulate and decrypt traffic with C2 and makes sniffing and passive monitoring at the network border more difficult.
EventBot also downloads an updated library which is encrypted with a different key coming from the C2 applying RC4 again. This library contains the majority of the information stealing and exfiltration capabilities.
Once executed on target, EventBot sniffs all the user navigation and does webinjects in Android applications specified, by package name, in the dynamic configuration. We’ve included a snapshot list of targeted package names in the appendix. Once sniffed, stolen information is sent to the C2 server over the channels previously established.
From all emerging versions we have collected, we have seen constant updates and improvements to the functionality of the malware. This resembles a software development product with new features and a regular release cadence including reliability improvements to web injects in recent versions. Most remarkable, we have seen new functionality for stealing all the Contacts from the Android user device, sending the contact list to the malicious server. This functionality is added from version 0.4.2.4 and we speculate that it’s in effort to further the malware’s distribution via SMS or other trusted contact spamming based on “sendSms” and "spamSms" strings found in our RE efforts.
Features
These newly discovered versions expand on EventBot’s capabilities list:
- web injects
- SMS theft
- sniff application activity, events, keylogging, usernames, and passwords.
- device information exfiltration: applications installed, OS, model, vendor.
- grab screen PIN
- (NEW) user contact list gathering
- (NEW) SMS spamming, possibly as a means to propagate
Requested Application Permissions
android.permission.ACCESS_NETWORK_STATE
android.permission.INTERNET
android.permission.READ_EXTERNAL_STORAGE
android.permission.READ_SMS
android.permission.RECEIVE_BOOT_COMPLETED
android.permission.RECEIVE_SMS
android.permission.REQUEST_COMPANION_RUN_IN_BACKGROUND
android.permission.REQUEST_COMPANION_USE_DATA_IN_BACKGROUND
android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
android.permission.REQUEST_INSTALL_PACKAGES
android.permission.SYSTEM_ALERT_WINDOW
android.permission.WAKE_LOCKStatic and Dynamic Configuration Structure
This malware makes use of two different configurations for the malware to work properly: static and dynamic (from C2).
Static Configuration
The static configuration format has been changed within the 0.4.x series.
The most relevant fields are:
- Malware Version
- Botnet ID
- 2 base C2 URLs for the first contact with the C2.
- Gate key: a static symmetric key for encryption/decryption of second stage and key derivation for shared session key for C2 communication.
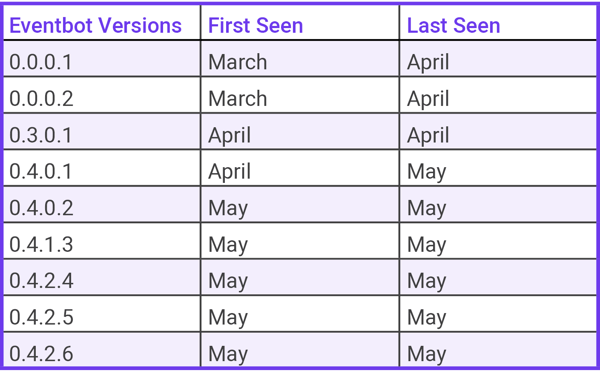
Malware Versions
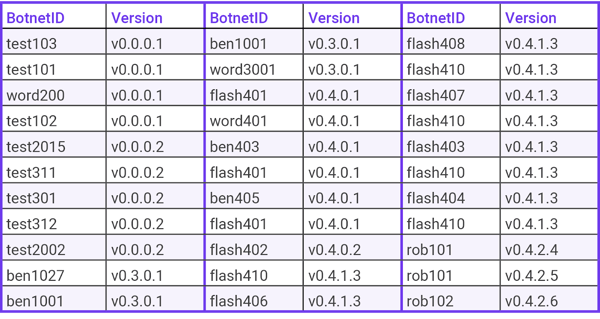
BotnetID
- Every APK sample is tied to a BotnetID segmentation, we get from this dataset a total of 22 different Botnets ID.
C2 Gate URLs - Sorted by versions
Version 0.0.0.1
- Gate URL 1:
hxxp://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f0_b - Gate URL 2:
hxxp://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0_b
. - Gate URL 1:
hxxp://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f0 - Gate URL 2:
hxxp://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0
Version 0.0.0.2
- Gate URL 1:
hxxp://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0_c
Version 0.3.0.1
- Gate URL 1:
hxxp://ora.blindsidefantasy[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://rxc.rxcoordinator[.]com/gate_cb8a5aea1ab302f0_c
Version 0.4.0.1 and 0.4.0.2
- Gate URL 1:
hxxp://pub.welcometothepub[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://marta.martatovaglieri[.]it/gate_cb8a5aea1ab302f0_c
Version 0.4.1.3
- Gate URL 1:
hxxp://free.zwifipro[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://pub.zwifi[.]pro/gate_cb8a5aea1ab302f0_c
. - Gate URL 1:
hxxp://free.timberlinetraders[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://pub.douglasshome[.]com/gate_cb8a5aea1ab302f0_c
Version 0.4.2.4, 0.4.2.5 and 0.4.2.6 - Latest active C2
- Gate URL 1:
hxxp://rob.charlotterobbins[.]com/gate_cb8a5aea1ab302f0_c - Gate URL 2:
hxxp://rob.sydneyrobbins[.]net/gate_cb8a5aea1ab302f0_c
Dynamic Configuration
- The Dynamic configuration is sent by one of the C2 Gate URLs coming in the Static Configuration.
- This is coming from the C2 as a Response to a Register device packet the malware sends in the Second stage from the malware following the encrypted method mentioned above.
- JSON Structure
- urls: C2 URLs
- webInj: Android package name apps targeted for injecting fake frontend overlay.
- aSniff: Android package name apps for sniffing.
C2 Gate URLs from Dynamic Configuration
- Gate URL:
hxxp://live.jescy[.]com/gate_cb8a5aea1ab302f0_c - Gate URL:
hxxp://craft.picturecrafting[.]com/gate_cb8a5aea1ab302f0_c - Gate URL:
hxxp://hani.stephaniegagne[.]com/gate_cb8a5aea1ab302f0_c - Gate URL:
hxxp://identitylive[.]online/gate_cb8a5aea1ab302f0_c - Gate URL:
hxxp://anna.anncarian[.]com/gate_cb8a5aea1ab302f0_c
Web Injects and Sniffer
At the time of writing, EventBot supports 28 Web Injects and sniffing over other 331 Android applications dynamically.
See appendix for more info about the targets.
How to find EventBot on PolySwarm
Since EventBot does not have the targets hardcoded in the binary or static payloads, it will make a request to retrieve them to the C2. PolySwarm’s threat intel staff have reverse engineered the C2 protocol and are actively adding second stage samples to our platform as we discover from stage 1 data already in the platform. Once we complete this process, we can find strings for companies affected and link several EventBot stages into one set of tags.
We use PolySwarm’s powerful Metadata Search feature for both of these steps:
- For tracking all the new samples coming in to the PolySwarm Network
- Feeding stage 1 samples to our C2 information gatherers
- Alerting customers when they’re targeted with samples added from step 2
Below we outline how an analyst would encapsulate this workflow for their own purposes.
Metadata Search
We can start by enumerating all samples, in all stages, that PolySwarm’s participating engines have marked as EventBot. The CLI is used for a metadata search that returns the SHA256 Hashes of the matching Malware Family field in Microengines:
$ polyswarm --fmt sha256 search metadata "scan.\*.\*.metadata.malware_family:*Eventbot*"|head -n 5 637ae1d4c61312d001e2cbd8b554514f30b8017febcf389782ea890428cbaef5 a7ab25033844978dd1b33f0aeddf77255f89734704586916a4064810600b72cd ddd8ffb901802de5d43ed2cbc97b8bf3a78c68e0f5289b5f92c8ee86a1989fa2 a9bbd0f92b9f66cd293dc1ff8a42b2aaf4d080c8e76dd009d746ab451e30a6af c7b47fe94b13ee8e49d3f415c5276adf8917902850a8bcb95e0e2bf4439c5099
We continue by examining filetypes from the query which provides a good rough-cut as to the stage of each sample:
$ polyswarm search metadata "scan.\*.\*.metadata.malware_family:*Eventbot*"|grep mimetype| head -n 5
Extended mimetype: Java archive data (JAR)
Extended mimetype: gzip compressed data, from Unix, original size modulo 2^32 1302840
Extended mimetype: Zip archive data, at least v2.0 to extract
Extended mimetype: Dalvik dex file version 035
Extended mimetype: Zip archive data, at least v?[0] to extract
You can further bound these queries to samples seen after Cinco De Mayo by adding a date constraint:
$ polyswarm search metadata "scan.\*.\*.metadata.malware_family:*Eventbot* and artifact.created>2020-05-05"
Alternatively, we can look for samples that only refer to a specific (known) C2 in an effort to quickly match segments to samples:
$ polyswarm --fmt sha256 search metadata 'strings.domains:free.zwifipro.com'|head -n 5
03e117f0fa50c64ca41ba6d2ee6334f2a78a1403280bda76059584446c2d6b9f
8cd3a1399115f085e310f925537e8bbddc9643bc7daa2fdd6d9888143a420ff5
a9bbd0f92b9f66cd293dc1ff8a42b2aaf4d080c8e76dd009d746ab451e30a6af
da6163ed732b4c5a06827caeca401ff68f9f8e7d6fef0967b81bb3ce6d9b2700
45632605b75db549da61f192f594ca6ef3dec54b06173304b424f840ec2faa3f
Or we can look for the “Gate” parameter to identify the C2 domains that follow the URL format.
$ polyswarm search metadata 'strings.urls:/.*gate_cb8a5aea1ab302f0.*/'|grep mimetype|head -n 5
Extended mimetype: Dalvik dex file version 035
Extended mimetype: Dalvik dex file version 035
Extended mimetype: Dalvik dex file version 035
Extended mimetype: Dalvik dex file version 035
Extended mimetype: Dalvik dex file version 035Understanding the findings
First Stage - APK
The first stage of the malware is usually an APK but in the recent versions it comes as a Flash Player Update (yes, it’s 2020). The package also contains the hidden TTF in assets/fonts/default.ttf that will be decrypted for running the second stage.
Our previous filetype metadata search reflects this and shows two different file types:
- Zip archive data, at least v2.0 to extract
- Java archive data (JAR)
And below is an example of a scan on one:
And the Static Config for that binary:
[+] BotnetID: rob102
[+] Eventbot version: 0.4.2.6
[+] Gate URL 1: http://rob.charlotterobbins.com/gate_cb8a5aea1ab302f0_c
[+] Gate URL 2: http://rob.sydneyrobbins.net/gate_cb8a5aea1ab302f0_c
[+] Gate Key: 7e89013da4660c162aae1a624080eb48b330e7148f32b0105869977614affd63Second Stage
The second stage is a false hidden encrypted TTF file (Font File) that contains the actual malicious code. This file is encrypted with the RC4 algorithm and loaded in runtime. It’s in charge of downloading the latest version library, running web injects, SMS theft, and most other malicious functionality. This is probably an evasion technique to prevent automated APK scanners from removing this app from distribution methods.
This second stage comes in two forms, reachable from metadata search:
Zipped Android Package:
https://polyswarm.network/scan/results/ace01aefac7f2e3f1baf84f350453d7bbd5a2b7bd26680c0c6fcd71e9a50afd1/details
Dalvik DEX file with the malicious class:
https://polyswarm.network/scan/results/file/a237d6ee717e7de68b7a176a5913641b53d463ab79673466690ce9a57c12f9ba
Malware Library Update
EventBot keeps itself updated calling out to C2 for an updated library. It will download a JAR file from the C2 encrypted with RC4 but this time the password will come in the C2 response along with the URL for downloading. For example the following sample:
Yields this download URL: hxxp://live[.]jescy[.]com/gate_cb8a5aea1ab302f0_c/524dc4f53af3c81cd9e150a509a67e3f71b59e1b8385d31ae04ba981bd56405a
Dalvik DEX file
Many kinds of Dalvik DEX files come from the metadata search labeled as EventBot, they could be from unzipped libs from the trojan as also modules from the trojan itself.
Here is an example from the decrypted second stage module:
Conclusion
PolySwarm will continue to track the latest versions of EventBot as they’re pushed out to infected devices. Please get in touch if you’d like to stay up to date with our latest findings!
The anti-malware community is invited to hunt for and download samples of these new versions of EventBot for free at https://polyswarm.network.
***Update 05/27/2020***
New Versions:
We have seen several new BotnetID and versions being propagated.
EventBot Version: 0.4.2.7 BotnetID: rob103
EventBot Version: 0.4.3.7 BotnetID: rob105
EventBot Version: 0.4.4.7 BotnetID: rob106
EventBot Version: 0.4.4.8 BotnetID: rob108/rob109
EventBot Version: 0.4.6.9 BotnetID: rob201
New C2 URIs:
Version 0.4.2.7 - 0.4.4.8 (rob108):
Gate URL 1: hxxp://rob.jmitchelldayton[.]com/gate_cb8a5aea1ab302f0_c
Gate URL 2: hxxp://rob.alanrmarble[.]com/gate_cb8a5aea1ab302f0_c
Version 0.4.4.8 (rob109)
Gate URL 1:hxxp://rob.selltokengarffhonda[.]com/gate_cb8a5aea1ab302f0_c
Gate URL 2:hxxp://rob.haileywilkinson[.]com/gate_cb8a5aea1ab302f0_c
Version 0.4.6.9
Gate URL 1: hxxp://cealegacy[.]online/index
Gate URL 2: hxxp://cealegacy[.]site/index
Note: All known C2 URLs (both static and dynamic) are currently down. Also it is important to note that the format of the latest C2 URL has now changed to remove the "gate_cb8a5aea1ab302f0" suffix at the end of the URI. This was a predictable progression as the old format was an easy target for searches and moving to a more dynamic URI would be a logical modification.
New Permission Requests:
Perform gestures - potentially perform actual gestures on the screen for the user (swiping, tapping buttons, activating/focusing certain areas on screen, etc.).
Request Delete Packages - Potentially could be used to remove apps that the malware wants to completely replace with malicious version
Send SMS - An upgrade from the Read SMS permission previously
We will continue to monitor this evolving malware and will send out updates of any additional important changes.
Complete this form to view the list of Android applications targeted by EventBot