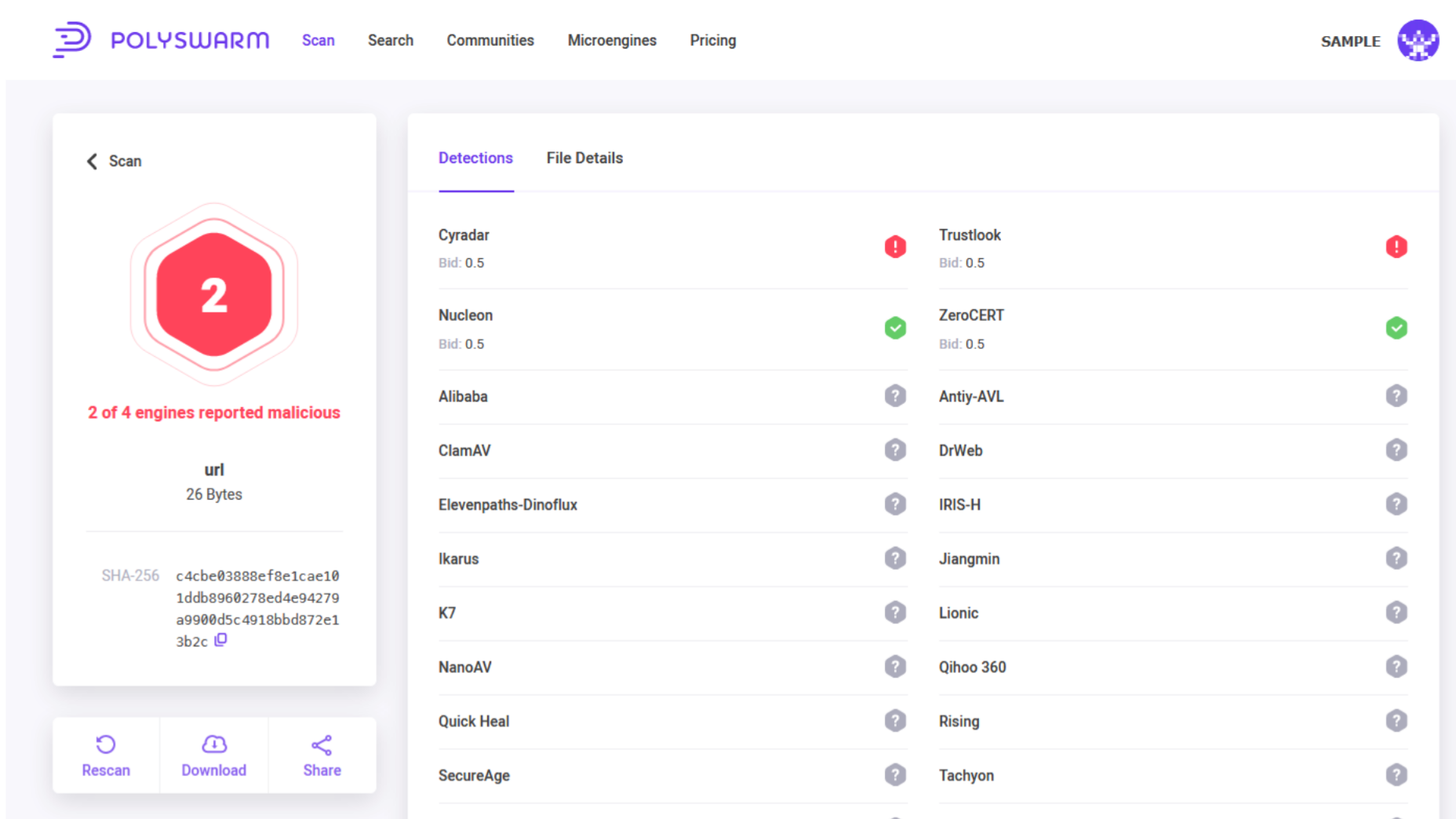
The PolySwarm marketplace launched earlier this year, giving users the ability to gain intelligence on files from a competitive network of crowdsourced scanning engines from around the world. Now, PolySwarm users also have access to real-time information on suspect URLs, domains, and IPs.
URL Scanning now available in PolySwarm
Aug 29, 2019 1:07:20 PM / by PolySwarm Team posted in Explained, PolySwarm, Product, Threat Bounty
Keynote from PolySwarm CTO at DEF CON: Blockchain-Security Symbiosis
Aug 20, 2019 4:20:04 PM / by PolySwarm Team posted in Explained, PolySwarm, Blockchain, Threat Bounty, Speaking, Events
Cybersecurity and blockchain technology share a symbiotic relationship. On one hand, blockchain ecosystems that aren’t secure, aren’t useful. On the other hand, blockchain technology unlocks new options for securing systems, infrastructure and more.
PolySwarm Co-Founder and CTO
Paul Makowski was invited to give the Day 2 Keynote talk at DEF CON Blockchain Village (2019) in Las Vegas. DEF CON (which follows on the heels of Black Hat) is one of the most well-known hacker conferences in the world, bringing together security researchers, cybersecurity experts, and other infosec people from around the world. Makowski presented
a thought-provoking talk examining blockchain and security from both sides of the coin: a look back at advances (and missteps) in securing blockchains and a look forward to security applications of blockchain technology. Watch the full presentation here: