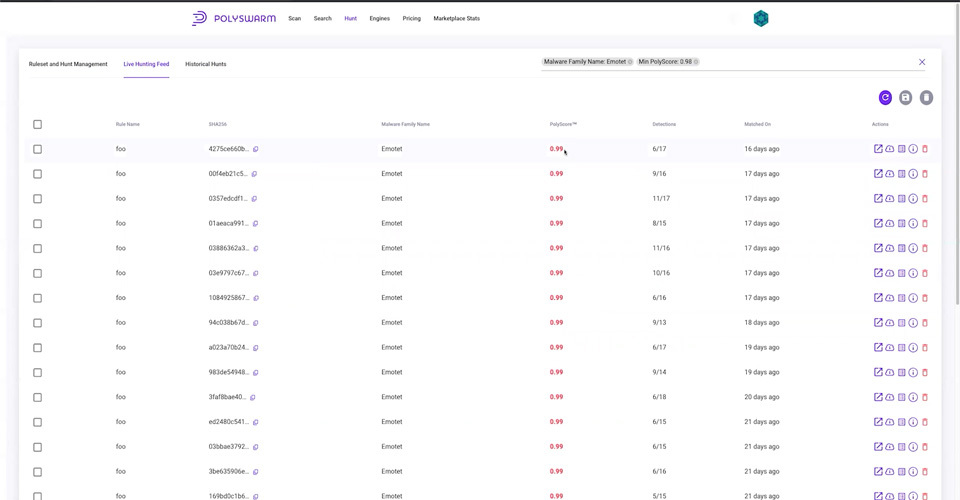
Many of you have given us feedback on our live and historical hunt functionality and we are thrilled to let you know that we are going live with your suggestions.
PolySwarms New Hunt Functionality
Jun 2, 2022 2:09:53 PM / by PolySwarm Tech Team posted in PolySwarm, Threat Hunting, New Features, Product Update
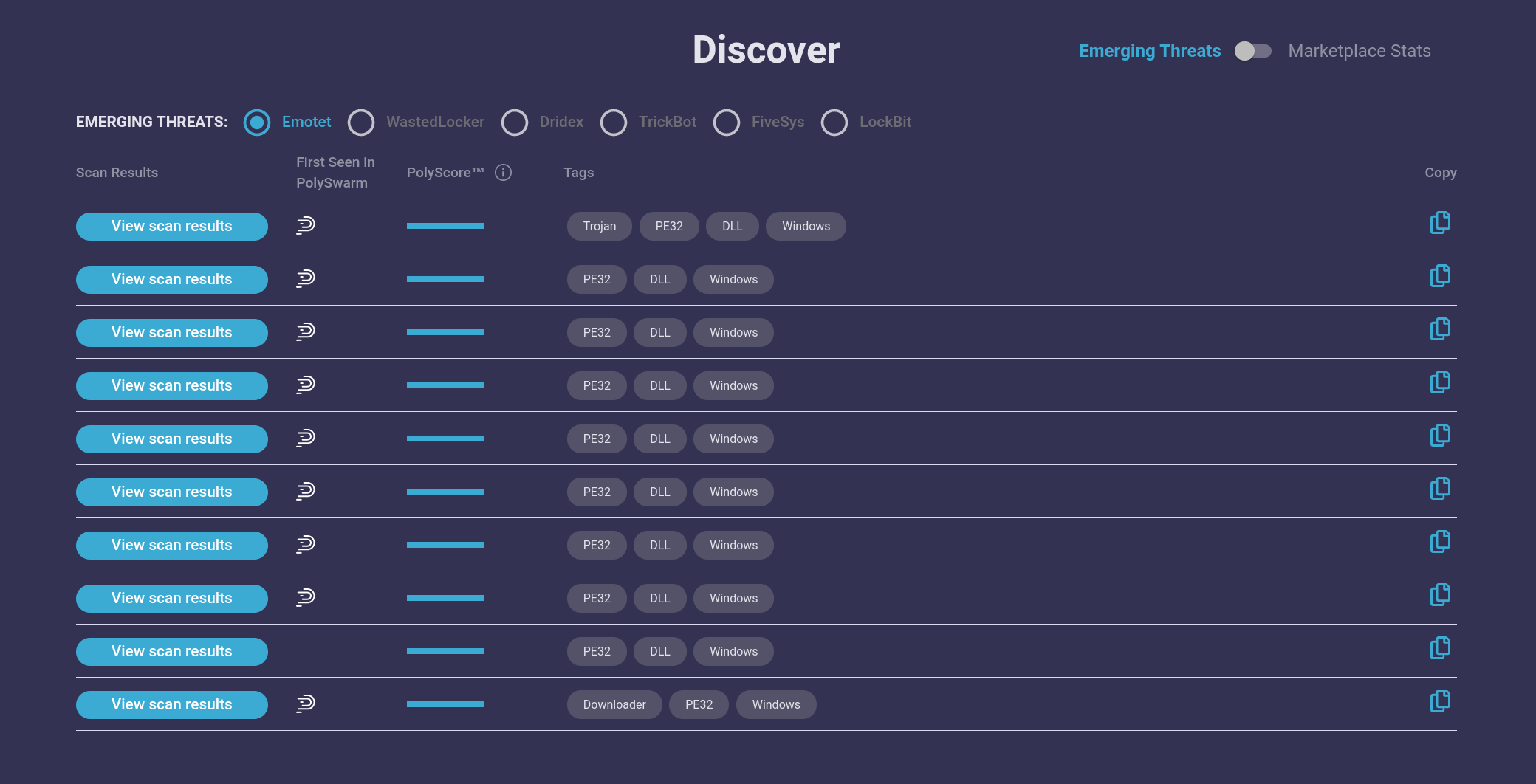
Emotet Banking Trojan Back in Action
Nov 30, 2021 3:25:13 PM / by PolySwarm Tech Team posted in PolySwarm, Threat Bulletin
Verticals Affected: Financial, Various
Victim Location: US, UK, Germany, Canada
Related Malware Families: TrickBot, Ryuk, QakBot, Zloader
A number of threat intelligence companies have recently reported on the return of the Emotet banking trojan. We first saw new variants of Emotet in our marketplace on November 15, 2021, before any industry in-depth analysis reports were released.
Why a New Engine Creation and Management Architecture?
Jun 16, 2021 11:57:47 AM / by Nick Davis posted in Explained, PolySwarm, Research
We recently completed the “New Engine Claiming and Management” milestone on our development roadmap. Our goal was to make it easier for Engine owners to build, configure and test an engine, and then join the PolySwarm Marketplace, so we’ve completely redesigned the architecture.
Security Telemetry: New utility use for Nectar (NCT)
May 17, 2021 6:05:27 PM / by PolySwarm Team posted in Explained, PolySwarm, Blockchain
Today we introduce a new utility use for PolySwarm’s Nectar token for average users: distributing rewards for security-relevant data about TLS certificates, DNS resolutions, and potentially malicious files encountered in daily computer use. Many of these telemetry sources are already collected from user devices by Antivirus (AV) providers. Still, there are a number of serious issues with how they are collected, how users are compensated for their information, and how these results are shared. By re-imagining how this marketplace works, we can increase collection transparency, fairly compensate all participants in the marketplace, and, most importantly, create a more unified source of security telemetry that will better protect users worldwide.
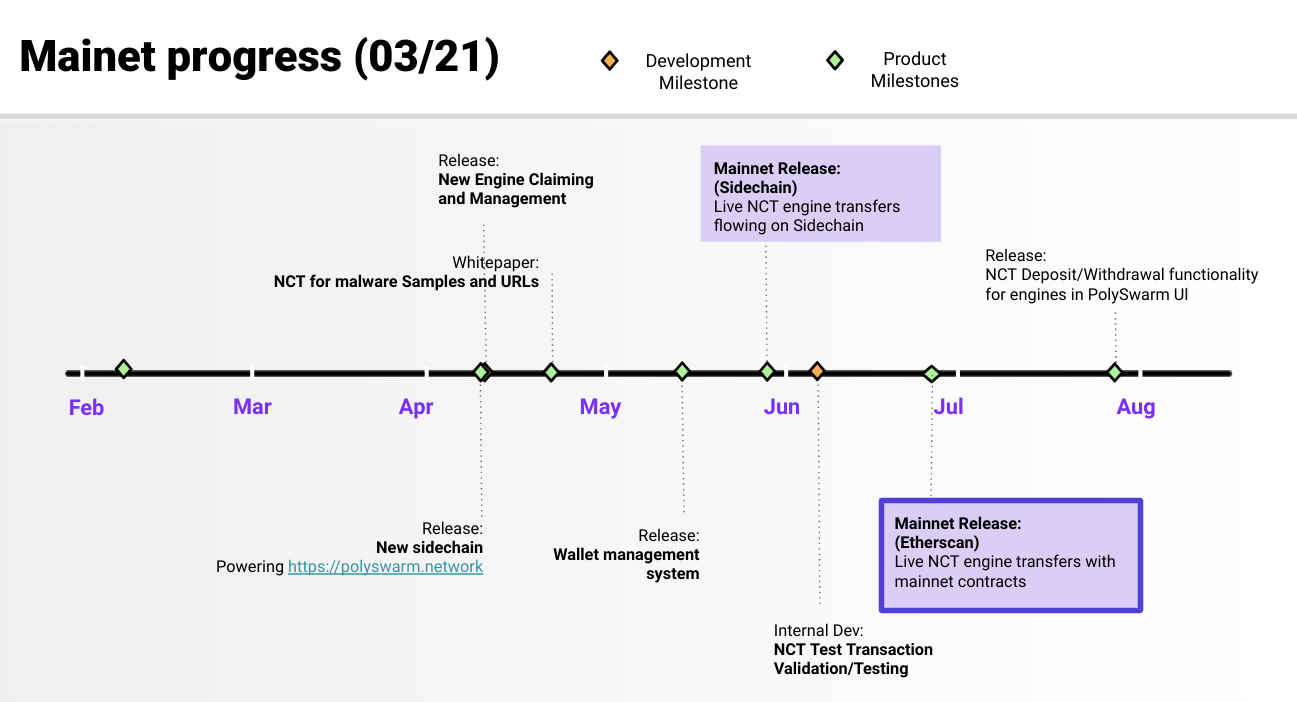
Progress to date and key milestones ahead
Mar 26, 2021 2:56:41 PM / by PolySwarm Team posted in PolySwarm, Product
The last 12 months have been intense yet very productive for PolySwarm, as we have scaled our platform, fast-tracked user acquisition and released new key features.
Let’s do a quick recap of what we’ve accomplished before we get into what lies ahead of us.
How to buy PolySwarm Nectar using Uniswap
Mar 24, 2021 1:32:06 PM / by Blake Reyes posted in Explained, PolySwarm, Blockchain
Introduction
So you’ve decided to buy PolySwarms’ token, and you think Uniswap sounds like the place to go? In this blog post we will go over the necessary steps you will need to take to buy your very own bag of PolySwarm Nectar.
PolySwarm now integrated with leading SOAR platform ThreatConnect
Apr 13, 2020 1:30:04 PM / by PolySwarm Team posted in PolySwarm, Product, Partner
Enterprises, OEMs, MSSPs can now access PolySwarm's novel file reputation and threat detection services via leading SOAR platform ThreatConnect, Inc.
ThreatConnect users can access PolySwarm--a crowdsourced threat detection tool, that enables better detection against new and emerging malware--for file reputation and threat intelligence. Cyber analysts using ThreatConnect's Security Operations Platform can download and operate the solution from a single pane of glass.
PolySwarm engine spotlight: researcher-driven engines detecting new and emergent malware
Mar 30, 2020 1:18:27 PM / by PolySwarm Tech Team posted in PolySwarm, Product, Research, Partner
To put it simply, there are some really cool threat detection technologies on the PolySwarm marketplace. As a recap, here at PolySwarm, we aggregate research-driven threat detection engines---both from AV companies and individual, specialized security experts---that compete in real-time to detect threats. Enterprises and individuals using PolySwarm benefit from deeper coverage of the malware landscape and unique threat intelligence from this aggregated network of engines.