Metadata can provide useful intelligence about the attributes, content, and functionality of an artifact (file, URL, etc.), giving malware analysts a foundation for understanding potential threats. Tools to support efficient malware analysis can be the difference between 15 minutes vs. 15 hours to triage and analyze a suspect artifact.
PolySwarm users - at any level, including the free Community plan - can now perform keyword searches through all the metadata PolySwarm has collected about every artifact, making it easier for researchers and incident response teams to find relationships between artifacts and gain useful insights.
In the PolySwarm ecosystem, we are ingesting huge amounts of file sets, all analyzed by a network of crowdsourced malware scanning tools from around the world. Beyond volume, PolySwarm offers unique, specialized engines, helping to detect zero-days and other harder-to-detect malware. By combining protection from all participating anti-malware engines with diverse domains of expertise, and economically rewarding accuracy of threat detection, PolySwarm provides broader, more accurate, and up-to-date protection.
Try PolySwarm Metadata Searching now at polyswarm.network
How to use Metadata Searching in PolySwarm:
All artifacts submitted to the marketplace are processed by our metadata analyzers. (The results of those analyzers can be viewed on the File Details tab on the Scan Results page if you are using the PolySwarm UI. If you are using the PolySwarm CLI tools, you’ll see all of the metadata in the JSON scan result object.)
Because of that first step and what we are announcing with this blog post, we now support the ability to search all of that metadata using elsaticsearch queries. (The full list of supported search keywords is available in our PolySwarm API/CLI documentation. To perform metadata searches in PolySwarm, we support the same functionality via both the PolySwarm UI and the PolySwarm CLI and API tools.)
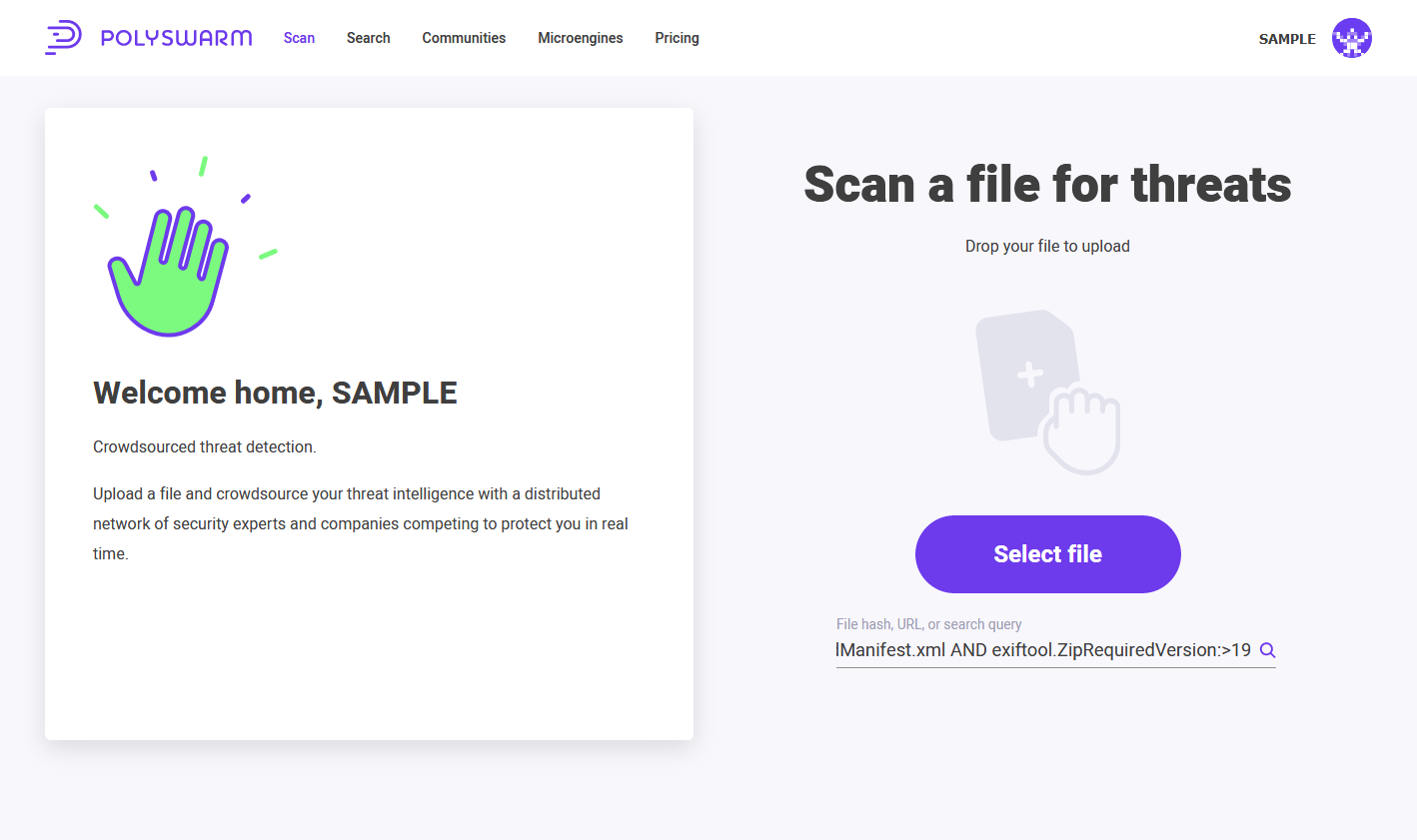
In the PolySwarm UI, a metadata search can be entered in the main search box on the Scan page.
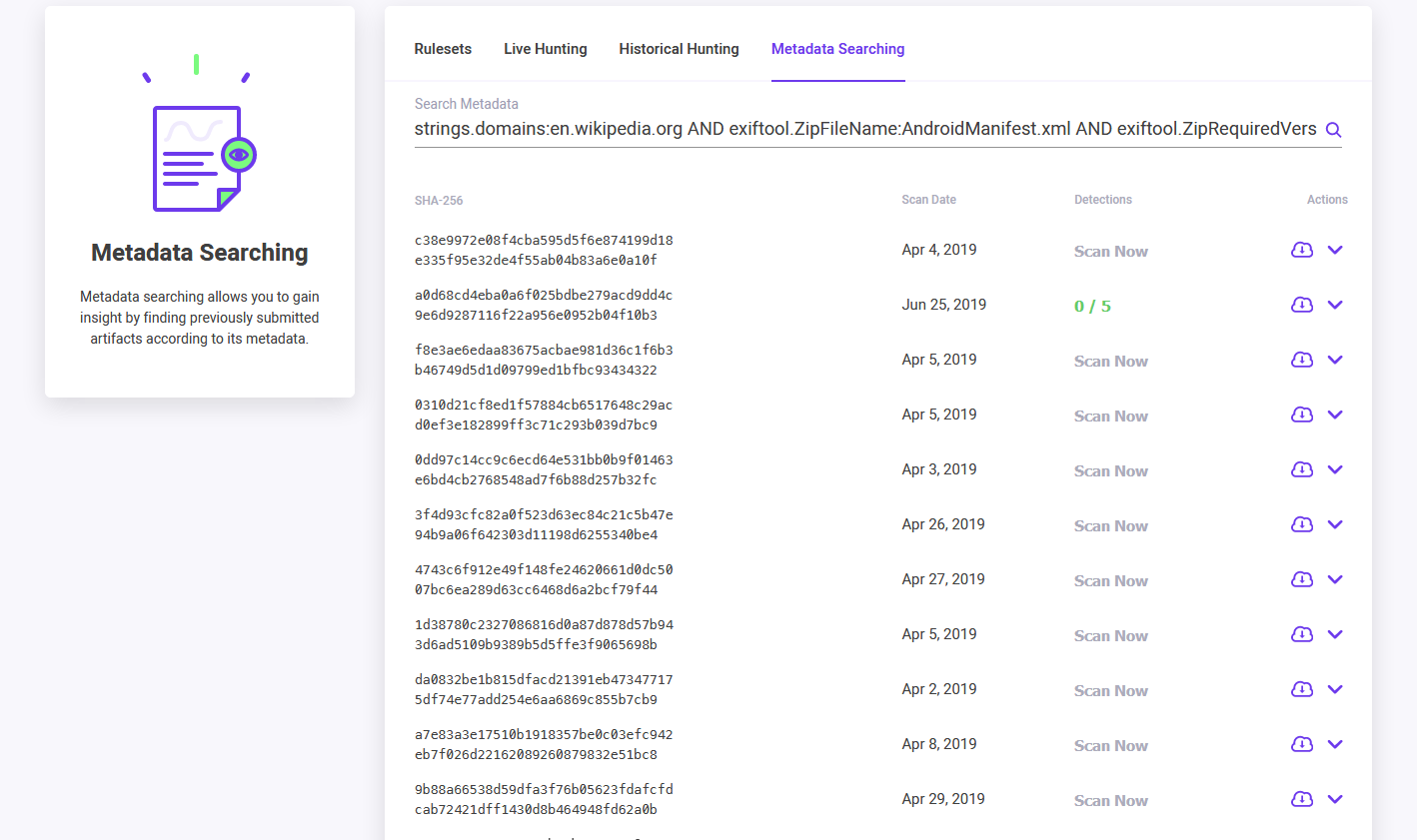
Or, users can go directly to the Search page and use the Metadata Searching tab to perform queries. Regardless of which location a user enters a search query, the search results are displayed on the Metadata Searching tab.
In the PolySwarm CLI, a metadata search can be entered using the 'search metadata' arguments.
Using the optional “-o /tmp/test.txt” argument, we are writing the output of the command to a text file for easy reading.
(Check out an example of PolySwarm Threat Hunting and Metadata Searching in action hunting a recent zero-day.)
***
Yes, there are other scanning aggregators out there that provide metadata searches, but PolySwarm is different in that it has a number of unique and specialized scanning engines, plus it provides more in-depth data that you won’t see aggregated in one place.
Many research tools are slow or are missing the multiple sources of data to be accurate and effective. This leads to false positives, incorrect analysis, and just bad data.
PolySwarm delivers a novel approach to threat analysis. Using PolySwarm is easy. Simply set up an account and get started!
