Recently, Cisco Talos released a report about a piece of fileless malware dubbed “Divergent,” a malware loader being used to infect victims with this previously undocumented payload.
“This threat uses NodeJS — a program that executes JavaScript outside of a web browser — as well as the legitimate open-source utility WinDivert to facilitate some of the functionality in the Divergent malware,” the research team noted in a blog post that details the threat. “The use of NodeJS is not something commonly seen across malware families.” They note that this malware can be leveraged to attack corporate networks and is likely designed to conduct click-fraud. And this malware is particularly tricky because it burrows deep within the host.
The Divergent malware was actually first seen in PolySwarm, before other multi-scanners like VirusTotal. Below, we show you how you can find malware details in PolySwarm using the IOCs (provided in the Talos report). And, without even running a debugger, malware analysts are able to extract important malware details from PolySwarm.
Overview of what we will cover
- URL scan of dropper and second stage hosting URLs
- Malware search using Hash Lookup of IOCs/hashes
- Malware search using PolySwarm Metadata Searching tool
- Malware search using a Yara Rule for Live Hunting
URL Scanning
Dropper
Let’s use PolySwarm CLI to scan the URL that was used to install a malicious remote assist tool. Run the following command:
$ polyswarm url https://uoibppop.tk
Scan report for GUID 2d73758e-a5f5-43f8-9711-f8663c07864b
=========================================================
Report for artifact url, hash: a951ab7047501b7df4b7c658ec2caff689a78e27041bd69e515598599243e5e1
Nucleon: Clean
Virusdie: Clean
Cyradar: Malicious, metadata: {'malware_family': 'malicious', 'scanner': {'environment': {'architecture': 'x86_64', 'operating_system': 'Linux'}, 'vendor_version': '', 'version': '0.1.0'}}
ZeroCERT: Clean
Second Stage
Next, let’s use PolySwarm CLI to scan 2 URLs used for the second stage Powershell malware hidden as PNG files.
To scan the first URL, run the following command:
$ polyswarm url http://1292172017.rsc.cdn77.org/images/trpl.png
Scan report for GUID 701659fe-70e2-41f1-ba65-78ec13061759
=========================================================
Report for artifact url, hash: 17cae7914970fec803e6e0cca15a3a705f580437f6da4f91b9913796f3420ad9
Virusdie: Clean
Cyradar: Malicious, metadata: {'malware_family': 'malicious', 'scanner': {'environment': {'architecture': 'x86_64', 'operating_system': 'Linux'}, 'vendor_version': '', 'version': '0.1.0'}}
Nucleon: Clean
ZeroCERT: CleanPermalink with these results: https://polyswarm.network/scan/results/file/17cae7914970fec803e6e0cca15a3a705f580437f6da4f91b9913796f3420ad9
To scan the second URL, run the following command:
$ polyswarm url http://1292172017.rsc.cdn77.org//imtrack/strkp.png
Scan report for GUID 6069f280-70e6-438a-a460-eae275080141
=========================================================
Report for artifact url, hash: 17ebd6367bef3b6d34a5b6718f3a528a8bf081eafd9cae8e0e569ac1edad2382
Virusdie: Malicious, metadata: {'malware_family': '', 'scanner': {'environment': {'architecture': 'x86_64', 'operating_system': 'Linux'}, 'version': '0.3.0'}}
Nucleon: Clean
Cyradar: Malicious, metadata: {'malware_family': 'malicious', 'scanner': {'environment': {'architecture': 'x86_64', 'operating_system': 'Linux'}, 'vendor_version': '', 'version': '0.1.0'}}
ZeroCERT: CleanPermalink with these results: https://polyswarm.network/scan/results/file/17ebd6367bef3b6d34a5b6718f3a528a8bf081eafd9cae8e0e569ac1edad2382
Hash Searching
In the news, there were 14 hashes for PE Files. Put those hashes into a text file, and then run the following command to look up those hashes in PolySwarm:
$ polyswarm search hash -r IOCs_SHA256.txtResult Summary:
- 7 files
- Dates:
- First seen: Sat, 27 Jul 2019 04:35:08 GMT
- First seen: Sat, 27 Jul 2019 06:14:30 GMT
- First seen: Sat, 28 Sep 2019 21:47:15 GMT
- First seen: Sun, 28 Jul 2019 08:57:25 GMT
- First seen: Sat, 27 Jul 2019 04:35:08 GMT
- First seen: Mon, 25 Mar 2019 19:39:04 GMT
- First seen: Tue, 26 Mar 2019 18:13:28 GMT
- Hash:
- SHA256: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
- SHA256: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
- SHA256: 2f4a9ef2071ee896674e3da1a870d4efab4bb16e2e26ea3d7543d98b614ceab9
- SHA256: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
- SHA256: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
- SHA256: a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
- SHA256: 607b2f3fd1e73788a4d6f5a366c708dbb12d174eba9863ade0af89ca40e1fdba
- Scan Results:
- Permalink: https://polyswarm.network/scan/results/file/ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
- Permalink: https://polyswarm.network/scan/results/file/a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
- Permalink: https://polyswarm.network/scan/results/file/2f4a9ef2071ee896674e3da1a870d4efab4bb16e2e26ea3d7543d98b614ceab9
- Permalink: https://polyswarm.network/scan/results/file/b2d29bb9350a0df93d0918c0208af081f917129ee46544508f2e1cf30aa4f4ce
- Permalink: https://polyswarm.network/scan/results/file/bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
- Permalink: https://polyswarm.network/scan/results/file/ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
- Permalink: https://polyswarm.network/scan/results/file/a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
- Permalink: https://polyswarm.network/scan/results/file/607b2f3fd1e73788a4d6f5a366c708dbb12d174eba9863ade0af89ca40e1fdba
Metadata Searching
Let’s try to find samples from this malware by its internal features. (Note: everything found from the searches are this malware family.)
By pefile.imphash
Let’s use PolySwarm CLI to perform a metadata search for the imphash: pefile.imphash:"2023fb6f54ebc52867881c8549c2fc62"
$ polyswarm search metadata 'pefile.imphash:"2023fb6f54ebc52867881c8549c2fc62"'Found 4 matches to the search query.
Search results for {'query': {'query_string': {'query': 'pefile.imphash:"2023fb6f54ebc52867881c8549c2fc62"'}}}
File a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
SHA1: 5b24a3b32d9dba95b296a7a16cbcf50a7df2d196
MD5: 08ac667c65d36d6542917655571e61c8
First seen: Sat, 27 Jul 2019 06:14:30 GMT
Observed countries:
Observed filenames: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File type: mimetype: application/x-dosexec, extended_info: MS-DOS executable
SHA256: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
SHA1: dd17b5d7442011effa2156c2470e7ad87e0435c0
MD5: 4bfc121ed751e5f5982e8cf207b1185c
First seen: Sat, 27 Jul 2019 04:35:08 GMT
Observed countries:
Observed filenames: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
File type: mimetype: application/x-dosexec, extended_info: MS-DOS executable
SHA256: a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
SHA1: a021803abe807323d43f0a26f55817d4f88ad84a
MD5: a42f269b966fd4cc700eb6a119470c22
First seen: Mon, 25 Mar 2019 19:39:04 GMT
Observed countries:
Observed filenames: a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
File bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
SHA1: 4d004abbc5a9085d713e6c3a79269c67f65484db
MD5: da8b478f6c1fa76858b67b1329bac447
First seen: Sun, 28 Jul 2019 08:57:25 GMT
Observed countries:
Observed filenames: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
By IPV4
Let’s use PolySwarm CLI to perform a metadata search for the ipv4 strings. We’ll use the ipv4 address from the C2.
$ polyswarm search metadata 'strings.ipv4:95.70.244.209' | tee -a polyswarm_metadata_search_ipv4.logFound 3 matches to the search query.
Search results for {'query': {'query_string': {'query': 'strings.ipv4:95.70.244.209'}}}
File a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
SHA1: 5b24a3b32d9dba95b296a7a16cbcf50a7df2d196
MD5: 08ac667c65d36d6542917655571e61c8
First seen: Sat, 27 Jul 2019 06:14:30 GMT
Observed countries:
Observed filenames: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File type: mimetype: application/x-dosexec, extended_info: MS-DOS executable
SHA256: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
SHA1: dd17b5d7442011effa2156c2470e7ad87e0435c0
MD5: 4bfc121ed751e5f5982e8cf207b1185c
First seen: Sat, 27 Jul 2019 04:35:08 GMT
Observed countries:
Observed filenames: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
SHA1: 4d004abbc5a9085d713e6c3a79269c67f65484db
MD5: da8b478f6c1fa76858b67b1329bac447
First seen: Sun, 28 Jul 2019 08:57:25 GMT
Observed countries:
Observed filenames: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
By lief.imported_functions
Now let’s try to find this malware from ‘Imported Functions’ with ‘AND’ operator, so we find the larger set of results for this specific malware.
$ polyswarm search metadata 'lief.imported_functions:"AdjustTokenPrivileges" AND lief.imported_functions:"LdrEnumerateLoadedModules" AND lief.imported_functions:"Sleep" AND lief.imported_functions:"OutputDebugStringA" AND lief.imported_functions:"GetCursorPos"'Found 4 matches to the search query.
Search results for {'query': {'query_string': {'query': 'lief.imported_functions:"AdjustTokenPrivileges" AND lief.imported_functions:"LdrEnumerateLoadedModules" AND lief.imported_functions:"Sleep" AND lief.imported_functions:"OutputDebugStringA" AND lief.imported_functions:"GetCursorPos"'}}}
File a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
SHA1: 5b24a3b32d9dba95b296a7a16cbcf50a7df2d196
MD5: 08ac667c65d36d6542917655571e61c8
First seen: Sat, 27 Jul 2019 06:14:30 GMT
Observed countries: ES
Observed filenames: a82dd93585094aeba4363c5aeedd1a85ef72c60a03738b25d452a5d895313875
File ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File type: mimetype: application/x-dosexec, extended_info: MS-DOS executable
SHA256: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
SHA1: dd17b5d7442011effa2156c2470e7ad87e0435c0
MD5: 4bfc121ed751e5f5982e8cf207b1185c
First seen: Sat, 27 Jul 2019 04:35:08 GMT
Observed countries: ES
Observed filenames: ba04eacaa80bb5da6b02e1e7fdf3775cf5a44a6179b2c142605e089d78a2f5b6
File a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
File type: mimetype: application/x-dosexec, extended_info: MS-DOS executable
SHA256: a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
SHA1: a021803abe807323d43f0a26f55817d4f88ad84a
MD5: a42f269b966fd4cc700eb6a119470c22
First seen: Mon, 25 Mar 2019 19:39:04 GMT
Observed countries: ES
Observed filenames: a7656ccba0946d25a4efd96f4f4576494d5f1e23e6ad2acc16d2e684656a2d4f
File bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
File type: mimetype: application/x-dosexec, extended_info: PE32 executable (GUI) Intel 80386, for MS Windows
SHA256: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
SHA1: 4d004abbc5a9085d713e6c3a79269c67f65484db
MD5: da8b478f6c1fa76858b67b1329bac447
First seen: Sun, 28 Jul 2019 08:57:25 GMT
Observed countries: ES
Observed filenames: bf2cdd1dc2e20c42d2451c83b8280490879b3515aa6c15ab297419990e017142
Live Hunting
Now that we have found some details and some unique features from this Malware, let’s create a Yara rule and enable a Live Hunt, so we can be alerted about future campaigns:
rule divergent_malware {
meta:
author = "PolySwarm"
description = "Divergent Fileless Malware"
strings:
$a = "\"accl\":"
$b = "\"acll\":"
$c = "\"version\":"
condition:
$a and $b and $c
}
While drafting this report, we viewed our Live Hunting results 24 hours later, and found some new samples that had been uploaded to PolySwarm:
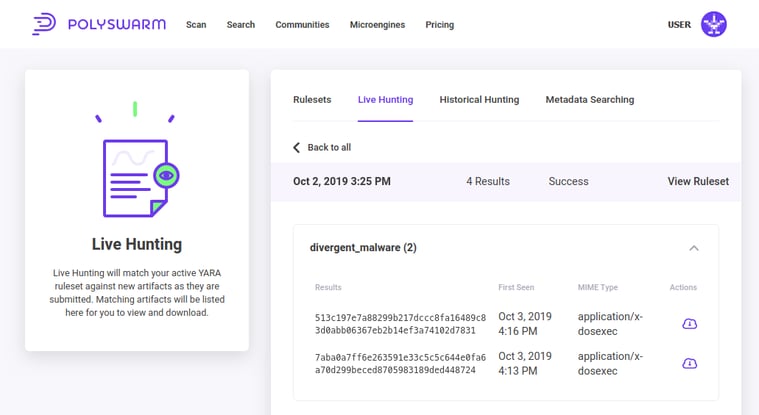
Examining the scan results of that first sample, we see that it is also clearly malicious:
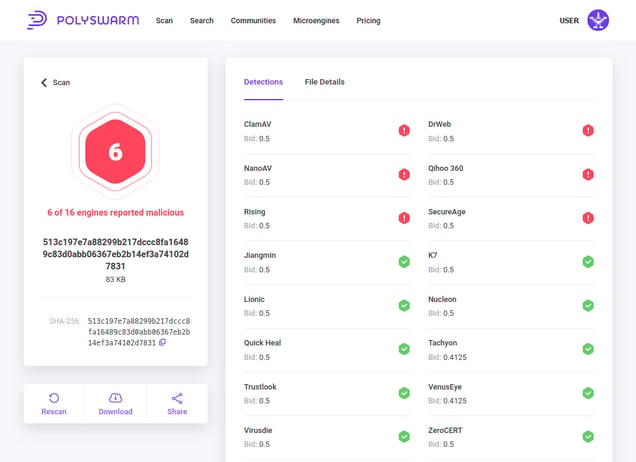
And if you look at the File Details tab of the scan results, you’ll get a full list of IOCs / C&C endpoints. Here is a screenshot of part of that list:
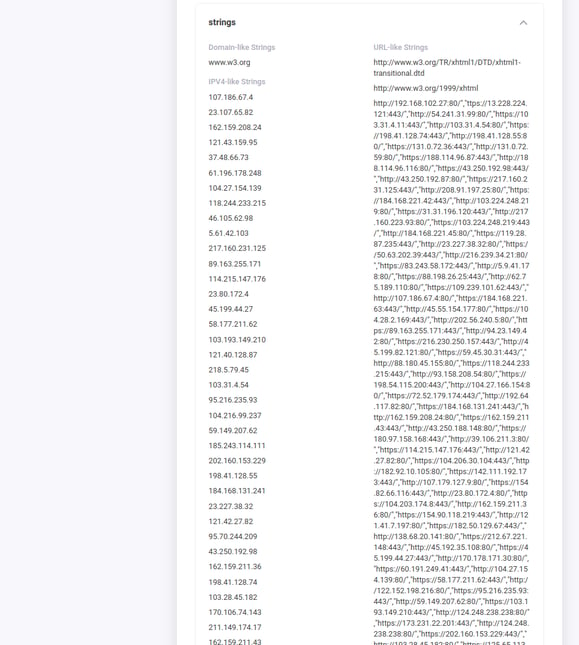
***
If you are not already using PolySwarm, try it out here. It’s free to use (however Threat Hunting and some other advanced features require a paid subscription). Simply create an account and start leveraging PolySwarm: https://polyswarm.network/