PolySwarm’s threat detection marketplace has created the possibility of a new type of cyber-related bounty: say hello to the threat bounty
First, came the bug bounty
Hunter & Ready launched the first known bug bounty program in 1983. Anyone who found and reported a bug within their operating system would receive a Volkswagen Beetle (aka Bug) in return. Over a decade later, in 1995, the term “bug bounty” was coined for the first time by a Netscape engineer.
Today, these types of crowdsourced security programs are widely used among tech companies and are often initiated to supplement internal code audits and penetration tests.
By crowdsourcing bug discoveries, large companies get to expand their internal teams and get to know about software vulnerabilities before they’re exploited. “Bug Bounty programs are much more cost effective than paying penetration testers or consultants,” claims Casey Ellis, CEO of Bugcrowd.
Smaller organizations are also starting to adopt and benefit as well from these programs thanks to an increasing number of companies offering bug bounty programs-as-a-service, with Bugcrowd and HackerOne leading the pack.
As a result, the increase in adoption has been exponential over the last years: HackerOne alone had over 300,000 ‘hackers’ registered in their platform by the end of 2018, which represents a 50 percent increase over 2017; and they almost doubled the amount of bounties awarded versus prior year. Despite the high growth experienced, the best is yet to come. Just 8 percent of Fortune 2000 companies used bug bounty programs in 2018, and Gartner estimates that crowdsourced security testing platform products and services will be employed by over 50 percent of enterprises.
Introducing the threat bounty

Threat bounty: Reward offered in exchange for an accurate determination of whether a digital artifact (URL, file, network traffic, etc.) is malicious.
Both threat and bug bounties tap into the concept of crowdsourcing, and leverage the wisdom of the the crowds to get a wider perspective, allowing enterprises to expand their internal security teams with diverse and specialized expertise in a cost efficient way. Both programs use economic rewards and include a competitive component to incentivize accuracy and quality outputs.

The nature of what hackers are looking for in threat bounties is different: It is about accurately determining whether an artifact (file, url, network traffic, etc.) is malicious, instead of bug / vulnerability discovery. In addition, threat bounties are automated, performed by software (‘microengines,’ as we call them) authored by security experts, allowing for near real-time ‘outputs’/answers. The automated component also enables successful security experts to generate passive income and make money while they sleep.
Although the average reward size in a bug bounty is larger, the frequency of bounties in a threat bounty is significantly bigger: A total of 100,000 vulnerabilities were reported in HackerOne in 2018, compared to an expected +1 million artifacts per day submitted into PolySwarm’s network by the end of this year. A big contrast!
Also, bug bounties reward the first hacker to report a legitimate vulnerability and/or bug, but threat bounties reward all accurate submissions within the allowed timeframe (usually seconds, depending on the bounty), allowing for multiple winners to split the pot.
Lastly, who holds the monetary (rewards) and validates submissions? In bug bounties, both roles are often done by the same entity, the company behind the bug bounty. In threat bounties, PolySwarm uses smart contracts to escrow funds and have independent arbiters doing the verification.
How threat bounties work on the PolySwarm marketplace

1) SUBMIT
Enterprises and MSSPs submit, via an API, millions of suspicious artifacts, daily, to PolySwarm’s marketplace.
2) COMPETE
Microengines scan all artifacts and provide assertions (malicious or benign) on those that fall within their expertise. They put their money where their mouth is: Along with their prediction, they are required to stake tokens to signal their level of confidence behind that assertion.
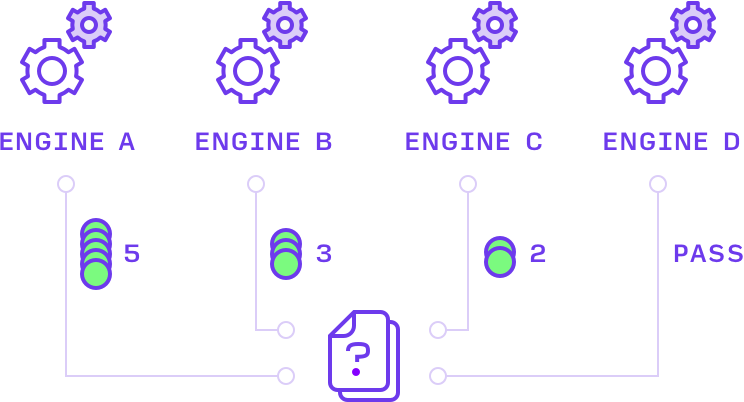
As seen in Engine D. Engines are not required to assert on all artifacts and can ‘pass’ when uncertain or outside their expertise.
3) VERDICT
All assertions are funneled back to the customer.

4) GROUND TRUTH
In one to two weeks the PolySwarm protocol converges on ground truth for that decision.
5) REWARDS
Engines that made the right assertion are proportionally rewarded (to the amount staked) with the tokens asserted by the engines that were wrong plus a portion of the enterprise subscription fees.

More about how the PolySwarm marketplace works here.
Same audience?
Do the hackers behind bug bounty and threat bounty programs share similar skills? Based on some data published by Bugcrowd there seems to be an intersection between these two audiences, as 22 percent of bug bounty participants claim to be experts in malware analysis, an important skill to succeed at threat bounties.
