Do you ever see a mysterious calendar invite appear on your Google Calendar? If the answer is yes, there’s a good chance you are the victim of a calendar invite phishing scam.
One of the latest schemes, detected on PolySwarm by one of its URL scanning engines Virusdie, is an attempt to drive a potential victim to a website to claim a free iPhone.
Here’s how it works
Attackers leverage a users default Google Calendar setting that enables ones calendar to automatically add any event and push a notification. The perpetrators simply preload the text on the event with a phishing link and a message enticing the target to click.
This scam we recently observed preys on a users potential interest in snagging a deal on an iPhone.
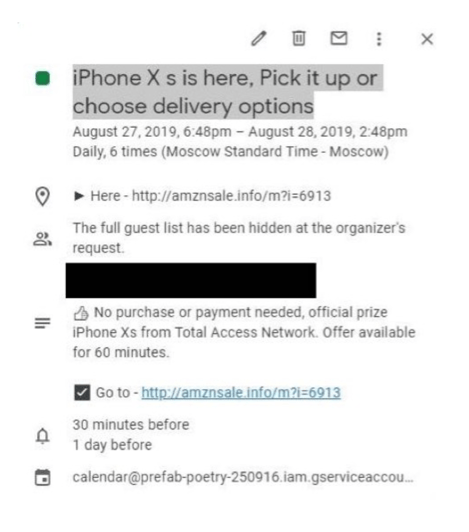
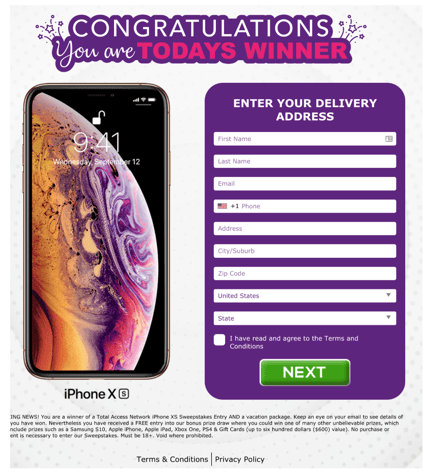
The perpetrators also cleverly set two reminders so the recipient gets two notifications leading up to the calendar invite date and time. Once you click the link and fill out the initial info on the page, you are prompted to input banking information (and give a weak explanation as to why you need to do so).
Google says it's aware of the issue and working on a fix
Yesterday, Google said they are working on a fix to address the ability of hijackers to access a users calendar and propagate it with these phony calendar invites. But in the meantime, The Verge put together an in-depth guide of some calendar tweaks to avoid getting these pesky invites.
How to avoid phishing scams
Never click on an unsolicited link. If you are unsure if it is malicious, drop it into PolySwarm’s free URL Scanner, or any other reputable checker to see if it’s flagged as malicious. If you receive an email or text message asking for you to provide any sort of sensitive information - or click a link to do so - don’t. Instead, call the company they are claiming to be and ask about the message. If you receive a Google Calendar invite from someone you don’t know, do not respond to it or click on any of the links. Simply delete it.
How PolySwarm finds lesser known malicious URLs
Here’s what makes PolySwarm different than other file and URL scanning aggregators: PolySwarm incentivizes its partner network of scanning engines, what we call ‘microengines,’ when they correctly assert on files and URLs. This is what we call a ‘threat bounty.’ The automated threat bounty encourages engines to only assert on files or URLs they specialize in or are confident in their answer, thus eliminating noise and inaccurate results often seen in other aggregation tools. PolySwarm also records all the results on the blockchain, so engine performance is immutable, and fully transparent for anyone to see.
Read more about how PolySwarm URL Scanning works, or try it out for yourself, here.
