PolySwarm is a threat intelligence marketplace where users upload suspect artifacts (files, URLs, etc.) and receive threat intelligence in return. While legacy multiscanners like VirusTotal, offer a similar service, they often neglect the confidentiality needs of malware analysts, researchers, SOC teams, etc. that want restricted access and/or deeper levels of control on malware-sample sharing.
PolySwarm Communities: Public vs Private
Mar 2, 2020 4:43:28 PM / by PolySwarm Tech Team posted in PolySwarm, Product
PolySwarm and Anomali integration: malware intelligence and enrichment APIs for ThreatStream
Feb 28, 2020 7:00:00 AM / by PolySwarm Team posted in PolySwarm, Product, Partner
As the volume and complexity of cyber threats increase, contextualizing and prioritizing incidents becomes critical. In addition to the well reported security shortage of talent in this industry, enterprise SOC teams are required to deal with an ever-growing queue of alerts.
SecureBrain joins the PolySwarm threat intelligence marketplace
Feb 6, 2020 11:42:48 AM / by PolySwarm Team posted in Product, Partner
Today PolySwarm, a marketplace for threat intelligence and malware detection, announces SecureBrain Corporation as its latest threat detection partner.
Video: How to use PolySwarm's free command line interface to get intel on malware
Jan 23, 2020 2:18:09 PM / by PolySwarm Tech Team posted in Explained, Product
Quttera joins the PolySwarm threat detection marketplace
Jan 17, 2020 12:07:00 PM / by PolySwarm Team posted in Product, Partner
“Quttera's unique and patented malware detection engine analyzes the bytes of information and weighs the parts of it that are suspicious. Quttera's technology is continuously enhanced with the security intelligence harvested from automated scanning of hundreds of thousands of websites worldwide. Self-learning and non-signature-based mechanisms incorporated into the core of the Quttera’s technology enables identification of the unknown (0-day) malware while improving the detection quality and precision of the malware scanning. We are happy to join forces with PolySwarm along with other top security vendors across the globe to deliver the best tools and services to fight cybercrime.” - Michael Novofastovsky, co-founder and CTO at Quttera
PolySwarm now integrates with Splunk Phantom
Nov 5, 2019 1:31:37 PM / by PolySwarm Team posted in PolySwarm, Product, Partner
Video: PolySwarm walkthrough - malware scanning and searching in PolySwarm UI
Nov 4, 2019 5:48:39 PM / by PolySwarm Team posted in Media, PolySwarm, Product
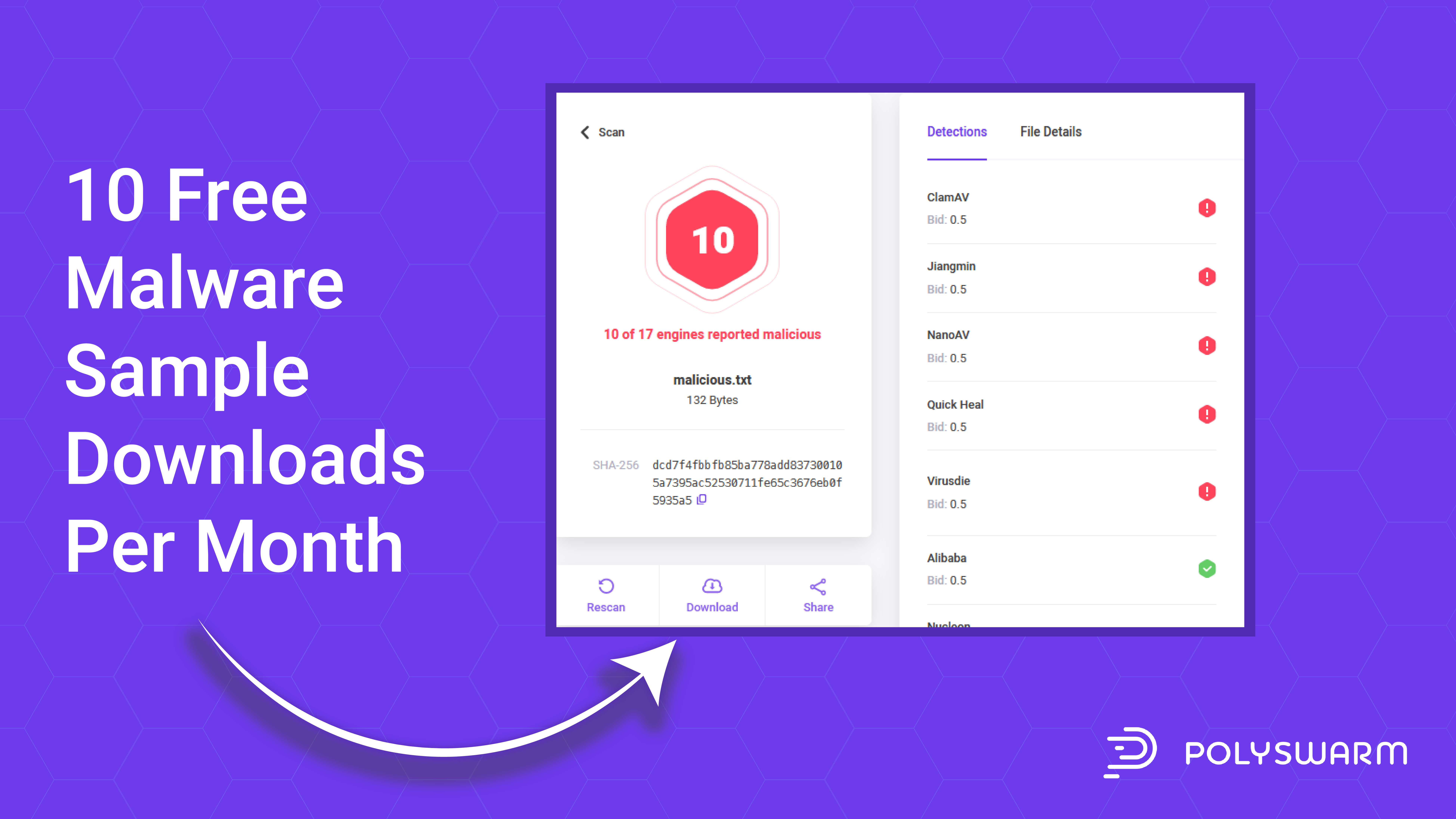
Free malware sample downloads, now available from PolySwarm
Oct 9, 2019 1:33:37 PM / by PolySwarm Tech Team posted in PolySwarm, Product, Research
PolySwarm users can now download malware samples completely free; sign-up for the free “Community” plan and get 10 malware-sample downloads per month.