The last 12 months have been intense yet very productive for PolySwarm, as we have scaled our platform, fast-tracked user acquisition and released new key features.
Let’s do a quick recap of what we’ve accomplished before we get into what lies ahead of us.
- We introduced key product features like PolyScore™, the ransomware feed and integrated sandboxing solutions to extract metadata details
- Integrated with leading threat intelligence platforms, to increase our reach and distribution
- Further developed our infrastructure, which allowed us to exponentially scale the volume of scanned samples and internal transactions we can process.
- Fast tracked user and customer acquisition, and increased the number of participating engines to 55.
New malicious samples (4x the scale)
New and emerging malware samples are disproportionately more valuable than “old” ones, since they are the most likely to go undetected by existing solutions.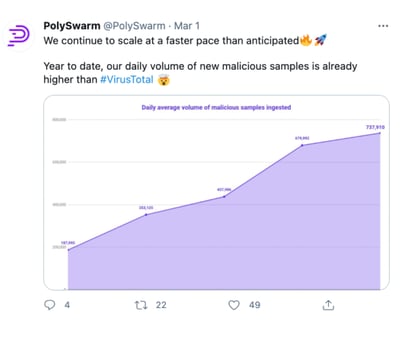 While others brag about the size of their database, which also includes old samples, benign ones, and duplicates, PolySwarm focuses on the daily volume of first scanned malicious samples. We care about new malware, what hasn’t been seen and/or it’s not yet widely distributed.
While others brag about the size of their database, which also includes old samples, benign ones, and duplicates, PolySwarm focuses on the daily volume of first scanned malicious samples. We care about new malware, what hasn’t been seen and/or it’s not yet widely distributed.
Over the last year, we’ve been able to grow that KPI by 4x, currently surpassing VirusTotal’s comparative volume during the same period.
To complement this metric, we also track the percentage of first seen samples against other multiscanners, as we always aim to optimize towards sample uniqueness and recency. Over the last year, we have been able to maintain a consistent range between 25-30% of the total, confirming we were able to scale without compromising the quality of those samples.
5 Million transactions a day
Every time an engine provides an opinion regarding the maliciousness of a given sample, staking tokens is required, and a transaction occurs.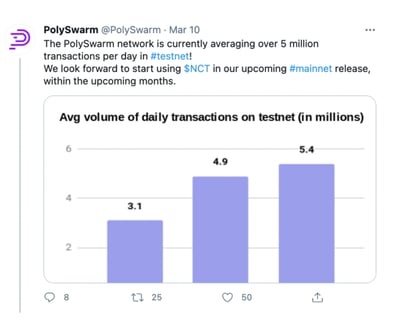
Engine Transactions include engines staking and payouts. Like a bug bounty, but automated and in real time and performed by threat detection engines instead of humans.
Post mainnet, $NCT will be used to:
a) Reward engines based on performance, to incentivize specialization and accuracy.
b) as a staking mechanism, to understand confidence levels from engines and prevent spam.
https://polyswarm.network/how-it-works
Engine Growth
PolySwarm’s network of suppliers continues to expand, and we now have 55 active engines operating within our marketplace. Our goal is to combine the wide coverage against common threats from commercial engines, with the ability to detect threats earlier from specialized ones.
We recently welcomed large and innovative players like Crowdstrike and Alibaba. Within the upcoming weeks 3 new engines will be joining the marketplace 2 of them are major companies within the antivirus and endpoint security industry. Make sure to subscribe to our blog to avoid missing any
Integrations
Aiming to further increase our distribution and reach, and become available within those tools where security experts and SOC teams spend most of their time, we’ve completed key integrations with leading Threat Intelligence Platforms (Cyware, Anomali and ThreatConnect), others more focused on incident response (Autopsy from Basis Tech) and SIEM/SOAR (Splunk and Demisto).
NEXT MILESTONES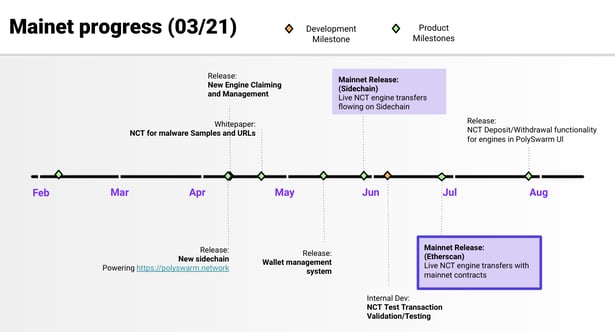
New engines on-boarded
Target Date: End of March - April
3 new engines will be joining the marketplace within the next weeks, 2 of which are major household brands within the antivirus and endpoint security industries. Make sure to follow us on Twitter (@Polyswarm) and subscribe to this blog to stay tuned.
Whitepaper release: NCT for malware samples and URLs
Target Date: Start of April
We will be introducing an additional use case for our NCT token, which will be described in detail in the upcoming whitepaper, to be released around mid April.
The essence: Users who contribute with malicious samples and urls that our customers and partners find value in, will be rewarded with our NCT token. We’ll build a browser extension to allow not just security experts, but also the average Joe, to participate and get rewarded. Think of it as the Brave for malware.We do envision a decentralized and distributed system where both engines and sample providers are compensated based on their contributions.
New Sidechain release
Target Date: First week of April
PolySwarm Nectar (NCT) natively lives on the Ethereum mainnet. Unfortunately, the Ethereum mainnet is far too slow and too expensive to support the sort of micro-transactions required by PolySwarm. By having a sidechain on top, we are able to improve:
- Scalability: Today, Ethereum does not scale (they're working on this of course), so applications must implement their own "Layer 2" scaling solutions if they demand low latency or high throughput transactions.
- Lower operational and maintenance costs.
- Higher speed and throughput.
- Confidentiality: PolySwarm supports the notion of limited-access, private Communities. This split-chain design makes that possible.
Target Date: End of May
This first mainnet release will require NCT to flow from the public Mainnet into our sidechain.
Along with that, we will release a ‘marketplace dashboard’ on the portal UI that will incorporate key activity metrics of the sidechain such as daily volume of NCT, with a weekly / monthly trend or the number of active engines, among others.
Target Date: End of June
This second mainnet release will enable NCT to flow from the sidechain back to the public Mainnet. As we stated above, the public mainnet cannot handle the rate of transactions required in our platform, so the transactions going from our sidechain to the public Mainnet will be less frequent. Users will be able to periodically transfer NCT between their sidechain wallets and public Mainnet wallets. That being said, most transactions occurring inside PolySwarm won’t be visible on Etherscan, given the mentioned use of a sidechain.
Join us in our upcoming AMA with Steve Bassi on April 15th, where he will provide a live update on these milestones and respond live to the community’s questions.
Onward!
