Verticals Affected: Financial, Various
Victim Location: US, UK, Germany, Canada
Related Malware Families: TrickBot, Ryuk, QakBot, Zloader
A number of threat intelligence companies have recently reported on the return of the Emotet banking trojan. We first saw new variants of Emotet in our marketplace on November 15, 2021, before any industry in-depth analysis reports were released.
Emotet was considered dead after its takedown by law enforcement groups in January 2021. Although leftover samples existed in the wild, there was no network infrastructure to support them. These samples were considered dead and aimless with no real purpose. We are seeing a rise of new, never-before-seen Emotet samples in our dataset. This surge of samples from our different sources have been identified and verified by our researchers as Emotet. These samples are currently highlighted in the Discovery section of our portal as first seen in PolySwarm compared to other scanning services.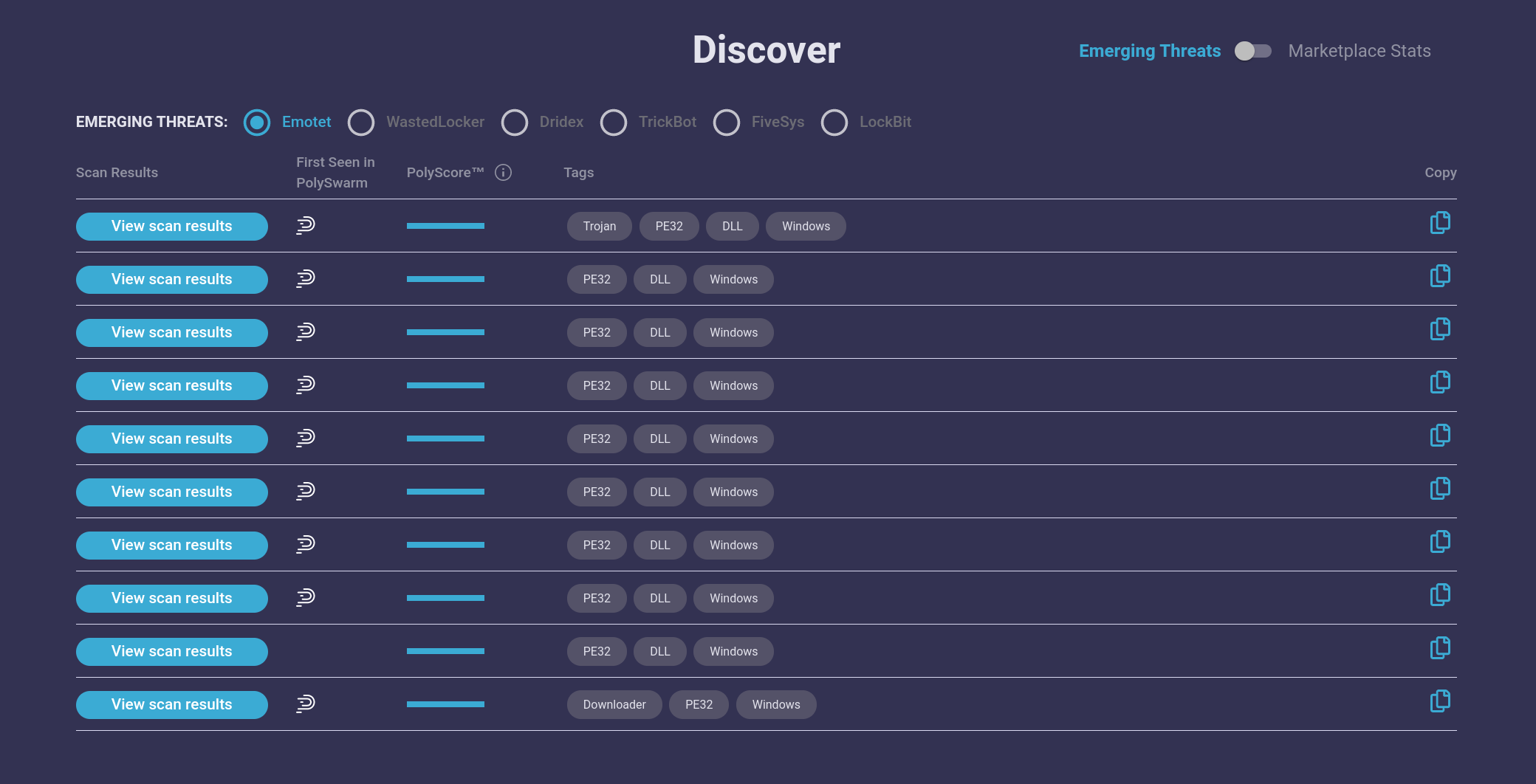
Previous versions of Emotet were extremely dangerous because they spread quickly, were difficult to detect, and were used by other threat actor groups to install ransomware, stealers, and other malware. It seems the Emotet group is back with a vengeance and will attempt to operate at the level of its former glory. This could result in widespread infection targeting financial institutions, hospitals, and retailers during the holiday season.
The Emotet banking trojan, first seen in the wild in 2014, was once considered the “world’s most dangerous malware.” The threat actors behind Emotet created an elaborate infrastructure, the notorious Emotet malware botnet. Emotet was used as a loader for other cybercriminals. Emotet gained access to organizations, and the unauthorized access was sold to other criminal groups. TrickBot, QakBot, Zloader, and Ryuk threat actors were known to use the Emotet botnet to gain access to targets.
We are currently tracking all new samples and extracting not only host behavior and command and control network channels, but the different botnet IDs associated with them as well. All of this data and information is available in our datasets for enrichment purposes.